Software as a Service of TOPdesk
Here you can find up-to-date information on our SaaS solution.
Read more about:
- Service setup and design
- Who does what?
- Certification
- Sub processors and hosting locations
- Hosting sustainability
- Always up-to-date
- Server management
- Security
- Availability & Continuity
- Access management
- Encryption
- Exit strategy
- Contact us
Service setup and design
TOPdesk SaaS is set up to deliver our services efficiently and effectively. Because we are highly specialized and able to automate all common tasks, we can provide our customers with a high quality service at a lower Total Cost of Ownership (TCO) than On-Premises hosting. This setup provides the following benefits to our customers:
- Data security by design. By maintaining data isolation per organization we provide multiple layers of security by design. Privacy and data ownership needs have been addressed, enabling our customers to use TOPdesk in a GDPR-compliant way.
- Customization and flexibility. Our SaaS platform offers customization and flexibility, allowing you to tailor features and workflows to meet your unique business needs.
- Ownership of data and exit strategy. Your company stays in control of your data. TOPdesk provides full access to all of your data. Backups will be provided in an open standard, during the contract and for a set period after your contract with us ends.
- Scalability. Our SaaS solution is designed to scale with your business, ensuring seamless growth and performance.
Hosting TOPdesk environments using industry-standard techniques like virtualization, resource sharing, redundancy and automation of operational activities results in lower TCO in comparison to On-Premises installation and high availability of the service.
Changes to TOPdesk are fully automated. Examples are: deployment of new production and testing instances for customers, adding or removing modules and functionalities, backups, updates and monitoring. This reduces the risk of human error and makes it possible to respond quickly to customer requests.
Who does what?
We keep TOPdesk running. The data center keeps the server running. And you are in control of the data.
Data Controller
- Decide which data is stored
- Decide who has access to the data
- Data processing agreement with TOPdesk
Data Processor
- Keep TOPdesk environments running
- Ensure the safety of data (stored and in transit)
- Data processing agreement with datacenter
Sub processor
- Keep the servers running
- Ensure internet connectivity
- Guarantee physical security of equipment
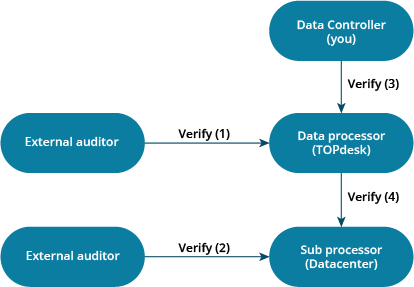
- An external auditor verifies that TOPdesk’s procedures are adequate to securely process your data, and verifies if TOPdesk acts accordingly (also see certification).
- The auditor of the datacenter ensures the security measures at each datacenter are up-to-date and working as intended (also see hosting locations).
- You can inspect the safety of your data at TOPdesk using the information on this page, and by requesting our audit report via your account manager. TOPdesk also has a template data processing agreement available, which you can use to formalize the agreements between TOPdesk as data processor and you as data controller.
- To verify the safety of the datacenter, TOPdesk has a data processing agreement with each datacenter used for hosting TOPdesk SaaS environments, and inspects the audit reports issued by their auditor.
These data processing agreements and audit reports ensure your data is kept safe, while you remain in full control of your data.
Certification
TOPdesk SaaS has an SOC 2 certification, which is audited annually, covering the previous period from April 1 to March 31. The certification report by the external auditor can be requested through your customer success manager (see Contact us).
SOC 2 has been chosen as the most applicable basis for reporting on our SaaS services. This international auditing standard is used to check if the risk management systems regarding security, availability, confidentiality and privacy are adequate for the desired goal, and verifies that the targets set by TOPdesk have been met in the previous period.
The SOC 2 certification also covers subcontractors. This means that TOPdesk verifies that the data centers used have sufficient (data) security measures, including relevant audits, and certifications on the services provided (also see Hosting locations and Who does what). Our auditor verifies that TOPdesk has requested and inspected the relevant certificates.
A SOC 2 certification always concerns the past, as the auditor tests whether the controls were sufficient during the time since the last audit. TOPdesk is committed to continue improving our security and procedures. If necessary, a bridge letter can be created to show the improvements we've made since the last audit.
Additionally, our SOC2 report includes a framework mapping, showing how controls of the ISAE 3000 SOC2 audit report map to ISO 27001.

Sub processors and hosting
List of sub processors
TOPdesk currently uses the following sub processors to help provide our TOPdesk SaaS services:
|
Name |
Purpose |
Data access |
Optional |
|
Manage infrastructure and process change requests for individual customer environments. |
Yes |
No |
|
|
Security Information and Event Management (SIEM) system, monitoring server logs and configuration files on the TOPdesk SaaS network to detect known attack patterns and threats. |
No |
No |
|
|
Manages SSL certificates for encrypting connections and adds additional security like DDOS protection. The Cloudflare Content Delivery Network is used to route traffic to TOPdesk SaaS environments. |
No |
||
|
Manage the hardware used to run all servers for our TOPdesk SaaS services. A detailed list of hosting providers can be found below. |
No. See encryption |
No |
|
|
The message bus enables the services within the TOPdesk application to communicate messages (data) to each other. This solution is active in all our Azure Hosting locations |
Yes, all data that is exchanged between our internal services traverses through the message bus. (More details about 84 Codes AB on My TOPdesk) |
No |
|
|
Allows TOPdesk to integrate and support Ebbot Live Chat and Ebbot AI Chatbot. |
Yes, only data actively shared with Ebbot Live Chat and Ebbot AI Chatbot. (More details about Hello Ebbot AB on My TOPdesk). |
Yes |
|
|
Allows TOPdesk to support and integrate with Insocial feedback solutions. |
Yes, only data actively shared with Insocial. (More details about Insocial on My TOPdesk). |
Yes |
|
|
Processing of user-provided content to enable AI Features. |
Yes, more info about Microsoft Azure OpenAI on My TOPdesk |
Yes |
Sub processors are only allowed access to customer data if this is absolutely necessary for the service they provide. For more details about what data can be accessed by which sub processors, and how long this data is stored, see KI 11787 in our knowledge base. TOPdesk holds all sub processors to the same security standards as we have for our own hosting services.
Changes in the sub processors will be announced in advance on our SaaS maintenance page, where you can subscribe for updates. Should you object to the use of a (new) sub processor, please contact TOPdesk Support or your Customer Success Manager to discuss which alternatives are available.
Optional sub processors only apply when you are using a specific service, which is not part of the standard package. As a customer you can check your contract to verify if one of them applies to you.
TOPdesk branches
All TOPdesk SaaS environments are managed from the European Union. Employees from our TOPdesk offices in the Netherlands, Belgium, Germany and Denmark are involved in managing TOPdesk SaaS environments. They ensure the infrastructure used to host TOPdesk SaaS environments is deployed and kept up-to-date. They also process change requests for individual environments. All processes at TOPdesk related to hosting SaaS environments are audited by an external auditor on a yearly basis. For more information about these audits, see Certification, or contact TOPdesk for a copy of the most recent audit report.
Hosting locations
TOPdesk currently offers hosting locations in Australia (AU), Brazil (BR), Canada (CA), the European Union (EU), Norway (NO), the United Kingdom (UK), and the United States of America (US).
Customers can choose where their environment is hosted and can verify this location via our customer service portal (My TOPdesk). Data is never moved to another region (e.g. from an EU hosting location to the UK or Norway) without the written confirmation from a SaaS main contact at the customer. Off-site back-ups are stored on a different location within the same region*, ensuring the same conditions apply.
All active data centers are listed below. You can find more details about our data centers and their (security) certification by visiting their websites.
Australia
|
Hosting location |
Primary site |
Backup location |
Hosting provider |
Data center provider |
|
AU1 |
Microsoft Azure via Microsoft Ireland Operations Limited (Certifications) |
Microsoft Datacenter (Australia) Pty Limited (Certifications) |
Brazil
|
Hosting location |
Primary site |
Backup location* |
Hosting provider |
Data center provider |
|
BR1 |
Microsoft Azure (Certifications) |
Microsoft do Brasil Importação e Comércio de Software e Vídeo Games Ltda. (Certifications) |
* For Brazil no off-site back-up in the same region is available at our hosting provider, so we use the best possible alternative until an off-site location in Brazil can be used at our hosting provider.
Canada
|
Hosting location |
Primary site |
Backup location |
Hosting provider |
Data center provider |
|
CA1 |
Microsoft Azure via Microsoft Ireland Operations Limited |
3288212 Nova Scotia Limited (Certifications) |
European Union
|
Hosting location |
Primary site |
Backup location |
Hosting provider |
Data center provider |
|
EU1 |
Microsoft Azure via Microsoft Ireland Operations Limited |
Microsoft Datacenter Netherlands B.V. (Certifications) |
||
|
EU2 |
Microsoft Azure via Microsoft Ireland Operations Limited |
Microsoft Ireland Operations Limited (Certifications) |
||
|
EU3 |
Microsoft Azure via Microsoft Ireland Operations Limited |
Microsoft Deutschland MCIO GmbH (Certifications) |
||
|
EU4 |
Microsoft Azure via Microsoft Ireland Operations Limited |
Microsoft Sweden 1172 AB (Certifications) |
||
|
EU5 |
Microsoft Azure via Microsoft Ireland Operations Limited |
Microsoft Deutschland MCIO GmbH (Certifications) |
||
|
EU6 |
Microsoft Azure via Microsoft Ireland Operations Limited |
Microsoft Datacenter Netherlands B.V. (Certifications) |
Norway
|
Hosting location |
Primary site |
Backup location |
Hosting provider |
Data center provider |
|
NO1 |
Microsoft Azure via Microsoft Ireland Operations Limited |
Microsoft Datacenter Norway AS (Certifications) |
United Kingdom
|
Hosting location |
Primary site |
Backup location |
Hosting provider |
Data center provider |
|
UK2 |
Microsoft Azure via Microsoft Ireland Operations Limited (Certifications) |
MSFT MCIO Limited (Certifications) |
United States of America
|
Hosting location |
Primary site |
Backup location |
Hosting provider |
Data center provider |
|
US2 |
Microsoft Corporation |
Microsoft Corporation (Certifications) |
All relevant data center certifications are reviewed by TOPdesk on a yearly basis.
Last review; March 2025.
Hosting sustainability
We strive to make our products as efficient and sustainable as possible. A large part of the environmental impact of our products comes from hosting our customers’ SaaS environments. All Microsoft Azure hosting locations operate carbon neutral and have been carbon neutral since 2012.

Always up-to-date
In TOPdesk, we believe in working in increments: thinking big and starting small. We’ve moved from releasing four major versions a year to quick and small releases. Small regular releases, also called continuous deployment, has many benefits over substantial updates.
We also use a staged roll-out process, where a new version is first released to a small group of test environments and is released to more and more environments while no bugs have been reported.
What does this mean for you as a customer? Your TOPdesk environment will be updated to the latest version every week! This means you'll always have the newest features and bug fixes.
Update groups
By default your test environment will be updated first, and the production environment at least one day later when no major bugs have been reported. 95% of our customers uses the default weekly updates to ensure they always have the latest features and bug fixes. For those who prefer to get updates even faster, we offer an early adopter update group. You can always choose to switch between the update groups in our customer portal.
| Update group | Update frequency |
|---|---|
| Internal tests | Daily automated tests and installation on an internal environment at TOPdesk |
| Test environments | Weekly updates to the latest version, when no problems were found during internal tests |
| Automatic early updates | Weekly updates to the latest version, when no problems were found on test environments |
| Automatic weekly updates | Weekly updates to the latest version, when no problems were found on test environments and in the early updates group |
Updates will always be installed during the maintenance window; between 22:30 (10:30PM) and 03:00(AM) of a time zone of your choice. Available time zones and more information can be found in our customer portal. Updating at night minimizes the impact for your end users.
Update notifications
Prior to the update of your environment, end users will be notified within their TOPdesk application of the upcoming update. This gives end users sufficient time to save their progress in TOPdesk.
Release notes
Our goal is to release functionality in small increments with minimal impact. You can visit our Release Notes website to review the changes to our software.
You can visit one of the following websites to stay up to date on our (future) developments:
- Big new themes are announced on our product roadmap (kanban / webinars).
- Changes in our software with a high impact are announced on our release notes page 6 months in advance. Important changes are also discussed in our regular product update webinars. You can subscribe for updates, so you'll have ample time to prepare.
- The release notes page is where you can find all changes, big and small, in our software. You can also open this page from within your TOPdesk environment (Menu > Help > Product news > Release notes) for an overview of relevant updates for your environment.
- You can share your suggestions and product feedback on our TOPdesk Innovation Platform. Here you can also see ideas from other customers, and vote on which idea you like most. You can register via My TOPdesk.
- We will send you an email when a bug that you reported has been fixed.
Server management
Using TOPdesk SaaS, you can rest assured your data is hosted on up-to-date hardware, running the latest security updates, and with all relevant server hardening methods. The TOPdesk SaaS network is completely separated from the TOPdesk corporate network, and all TOPdesk SaaS servers are deployed automatically and registered in our CMDB. This has numerous advantages:
- The automated server deployment, configuration and recovery ensures that disruptions don’t impact information security, as replacement servers will always be deployed using a secure, hardened, and tested configuration.
- Servers are always automatically configured to only allow connections on ports and protocols required for the specific task the server was designed for. No other connections are allowed.
- Hardly any manual configuration of servers is required, reducing the possibility of manual errors. An automated system verifies all configuration files are set to the correct values every 30 minutes, overwrites all changes that may have been made, and reports on the network status.
- Servers are constantly monitored, and servers that are no longer needed are removed on a regular basis. There are no unmanaged devices in the network.
- Software updates can be installed easily, using staged roll-out. Updates are installed on a monthly basis, and are first installed on non-critical servers to check for compatibility issues. Critical security updates are installed on all relevant servers within a week.
- Recovering from a site failure is very similar to standard operations, as creating the required new servers is similar to the automated deployment of new servers in our current network. This happens regularly, as our SaaS customer base is constantly growing.
- The clocks of all servers are synchronized to approved time sources.
Management access to the TOPdesk SaaS network is only possible from a secure multi-factor authentication gateway server, using a personal account with sufficient permissions. Access to this gateway server is closely monitored, and the multi-factor authentication set-up ensures administrators are always directly personally notified when someone tries to misuse their credentials.
As the TOPdesk SaaS network only consists of virtual machines on servers in professional data centers, there is no need for removable media (USB drives), WiFi connections, printers, and other common office devices. This reduces the attack surface of our SaaS network, and prevents malware infections.
Security
At TOPdesk, we take your data security seriously. Recognizing that security is an ongoing process, we continually strive to improve the security of our hosting services, software and internal procedures. You can read more about our security efforts below and on our TOPdesk Tech Blog:
On the Contact us section of this page you can find more information about reporting security issues.
Secure hosting
We only allow secure connections to TOPdesk SaaS environments. HSTS preloading is used to ensure all common browsers force users to a secured connection. The strength of our SSL certificate (used to encrypt the connection) is evaluated on a regular basis and currently has an A+ score from Qualys SSL labs.
TOPdesk uses a Content Delivery Network (CDN) for worldwide fast availability of TOPdesk environments, for (D)DOS protection and to block known threats. A Security Information and Event Management (SIEM) system is used to detect attacks against our network in an early stage. These systems are monitored 24/7 by a Security Operations Center with certified security experts.
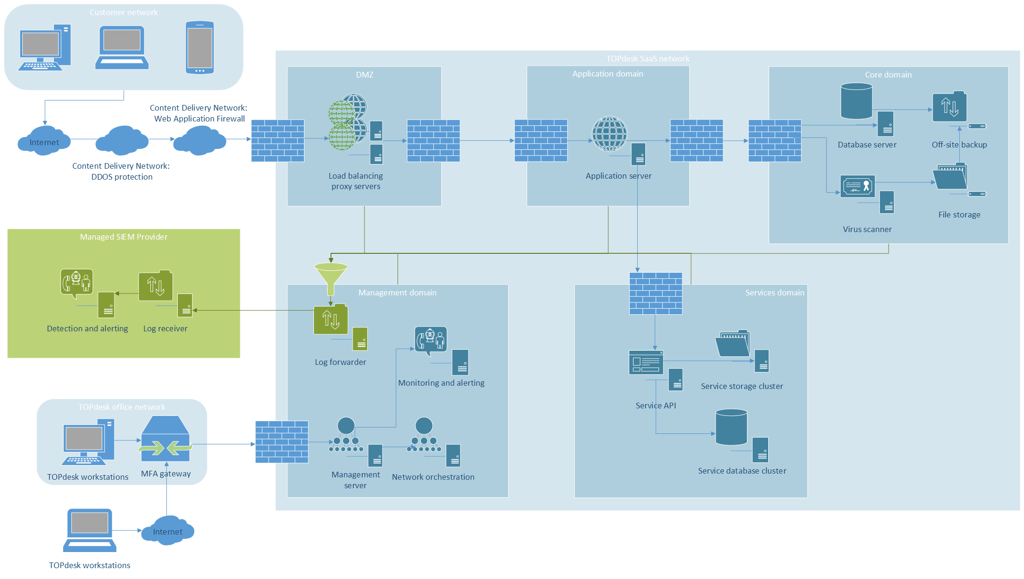
Click the image for details
Additionally, you can use your own intrusion detection system and link this to the TOPdesk (access) logs. It's also easy to set up an IP restriction for your TOPdesk SaaS environment, so only your colleagues have access your TOPdesk environment.
Antivirus and malware definitions are updated multiple times a day. Files are scanned upon opening and during upload, ensuring your users can safely work with attachments.
Servers are hardened by only allowing predefined connections, setting all relevant security settings and monitoring these settings against a desired state. TOPdesk will also ensure all relevant updates are installed in a timely fashion (see Server management and Always up to date).
Management access is limited to a small group of TOPdesk SaaS administrators and is only possible using a personal account and via a multi-factor authentication (MFA) gateway (see Access management). Separate servers are configured for management access, which are hardened and closely monitored.
Data separation
Your data is stored separate from other customers' data. Customer specific files (like attachments) are stored in a folder which can only be accessed by your dedicated TOPdesk environment. Folder and file permissions ensure that only the TOPdesk environment that created a file can access it.
This design also ensures that malware can't spread within our SaaS network. Only your TOPdesk environment can access your files and doesn't have permissions to execute something, or to access files outside your folder, preventing viruses from spreading.
A similar design is used for the database management; your TOPdesk environment can only connect to it's dedicated database, and database permissions ensure that no application but your TOPdesk environment is allowed to access the data. This dual layer of security ensures that data remains segregated from other customers, and can never be accessed by unauthorized users.
Secure software development
Secure coding guidelines ensure our software is of high quality and safe to use. Our measures include:
- An extensive internal 'Definition of Done' which defines minimum standards for all software that is developed. These standards include topics like; accessibility, privacy, security, error handling, API usage, and much more.
- Using pair programming and code reviews to ensure adherence to our standards and code quality.
- Following secure coding guidelines and continuously testing on topics mentioned in the OWASP list.
- Using standard frameworks and methods to prevent vulnerabilities resulting from programming errors.
- Employing security-specialized developers who initiate knowledge sharing and peer reviews at our Development department.
- Actively keeping track of security issues with external methods used by TOPdesk. This way, we can take follow-up action if such an issue is found.
- Combining automated and manual tests during development and delivery phases.
- Getting external parties to evaluate all our versions before they go live on your production environments.
Penetration tests
During development all software components and dependencies are scanned for known vulnerabilities. If no problems are found, the software is compiled and automatically tested. When all tests are successful, the software is deployed on a live environment which is scanned (black-box) for vulnerabilities on a daily basis. A daily automated penetration test verifies if common or previously found issues can be exploited. These tests include known threats and OWASP vulnerabilities.
The daily automated vulnerability scans and penetration tests are executed by an external auditor. To verify the scan results, improve future scans, and detect new issues specific to the TOPdesk software, a certified independent security expert performs a security test at least every 3 months. If the security test, penetration test, or vulnerability scan results in any actionable findings, TOPdesk will resolve these with the highest priority.
You can also execute your own penetration test or vulnerability scan, but please inform us beforehand.
These efforts have led to an SOC 2 audit report (see certification), which you can request to verify the security of our procedures and processes.
Availability & Continuity
We aim to keep all TOPdesk SaaS environments online 24/7. Our target uptime in the standard SLA for TOPdesk SaaS production environments is 99.9%. The average uptime of all TOPdesk SaaS production environments (24/7, excluding scheduled maintenance) in Q3 2025 was 99.99%.
For test environments we strive to maintain the same high availability, however they're not included in the SLA as they may be subject to necessary interventions for providing the SaaS production environments uptime level like troubleshooting, testing purposes or load balancing, which can result in lower availability compared to production environments.
Several measures ensure the availability of TOPdesk SaaS environments:
- Our redundant infrastructure ensures that a failing part does not affect availability.
- TOPdesk is running on virtual machines that can be instantly transferred to another server, should a server fail.
- The TOPdesk database is stored on servers with redundant availability, performing an automated failover and ensuring availability in case of a database server failure.
- Several proxy servers in a load balancing set-up ensure heavy traffic does not cause your TOPdesk environment to become unreachable.
- Automated deployment of servers from a CMDB ensures failing servers can be quickly recreated.
Monitoring and incident response
TOPdesk has a 24/7 monitoring system on all TOPdesk SaaS environments and servers. The monitoring system verifies health metrics for every TOPdesk environment, like the (internal and external) availability, database connection and search index availability. Servers are also monitored on relevant metrics e.g. availability, CPU usage, memory usage and available disk space. To ensure our back-up system works as expected, we also monitor the last back-up restore test for database servers.
Should the monitoring system detect a problem, TOPdesk operators are immediately notified. During the night, a 24/7 stand-by shift ensures issues are quickly resolved. Issues affecting multiple TOPdesk environments are published on our status page and via My TOPdesk. You can also verify the monitoring results for your environment(s) on our portal, and (if desired) immediately schedule follow-up actions like a restart of your TOPdesk environment, or submit a ticket for our Support team.

Back-up procedures
Back-up procedures ensure we can continue to operate in the unlikely event that an emergency occurs, and data becomes unreachable:
- Continuous database transaction logs ensure that we can recover the set of databases of every entire hosting location from any point in time for the past 30 days if a disaster should occur
- Daily off-site attachment back-ups ensure your uploaded documents also remain available, even in case of a data center failure.
- If you'd like to store a local copy of your database, you can easily request an export of it using My TOPdesk.
Back-up and restore procedures are tested at least monthly. A monitoring system ensures the last restore test for each site was no longer than 30 days ago. As servers are deployed automatically, recovering from a data center loss is hardly different from day to day operations.
Disaster recovery procedures
Our disaster recovery procedures and back-up systems ensure quick recovery times. In over 75% of all cases we are able to restore all services within 15 minutes.
In case of serious failures within a site, redundancy and fail over procedures ensure:
- Recovery Time Objective (RTO): 1 hour.
- Recovery Point Objective (RPO): up to 60 minutes. In most cases less than 1 minute, using Point in Time restore possibilities.
In the unlikely event of a total site failure (datacenter is lost):
- Recovery Time Objective (RTO): services are fully operational for all customers of the lost site, within 5 days.
- Recovery Point Objective (RPO): a maximum data loss of 24 hours is possible.
You can always stay up-to-date regarding the availability of TOPdesk SaaS environments by checking the availability of your environment on our customer portal (My TOPdesk) and by visiting our SaaS Status blog.
Access management
Access for users
TOPdesk can link to many identity providers (IdPs) meaning you can easily control who has access to your TOPdesk environment, without setting up a separate login system. Simply link TOPdesk to your existing IdP and you can log in using Single sign-on (SSO) including all your security requirements like multi-factor authentication. Our consultants can help out to create a secure link between both systems.
TOPdesk allows for role-based interfaces and authorizations, and access is adjustable on a granular level. You can choose which services each user (or user group) has access to, and whether the user has read, write, or advanced permissions. Roles and permission groups can be easily defined and changed in the interface by selecting the appropriate permissions through checkboxes.
Via our customer portal (My TOPdesk) you control your TOPdesk SaaS environment. You can manage which users are allowed to request changes to the environment, schedule actions and request other changes. TOPdesk will only execute changes requested by contacts that have previously been registered as 'SaaS Main Contact' person in our system, to prevent unauthorized changes.
Access for TOPdesk
TOPdesk employees will only access your TOPdesk SaaS environment when you have requested them to do so, for instance when you’ve asked our Support team for help.
All TOPdesk Support staff that might be granted access to your environment will have:
- a certificate of conduct
- a confidentiality agreement in their contract
- completed an extensive training program regarding the TOPdesk products, and hosting related topics such as handling confidential data and security awareness.
You can even determine whether TOPdesk employees can access your TOPdesk environment and limit this to your geographical region. This way you can e.g. limit or grant access to employees of a specific TOPdesk branch. You can configure this via Functional settings > Login settings > Remote Access for Support in TOPdesk.
TOPdesk won't store any passwords for your environment, TOPdesk employees will only access your environment using a personal account from a secure TOPdesk authentication server.
Access controls
You can (automatically) download the access logs for your environment to verify who accessed the environment, and at what time. Access logs include all login attempts and information to identify the source, like IP addresses. As the access logs can be accessed automatically, you can link them to your own Intrusion Detection System.
TOPdesk stores access logs for half a year. If you'd like to store the logs for a longer period, you can download a copy.
You can also request to make the full TOPdesk logs available for automated access. This allows you to review all activity in your TOPdesk environment, including settings changes, permissions changes, and new accounts. The full TOPdesk logs will be available for up to 3 days, but you can store a local copy if you need them longer.
It's possible to limit the availability of your TOPdesk environment to a certain IP range for additional security. To request an IP allow list, use the form on our customer portal.
Also see our privacy policy and the Security section of this page.
Encryption
Data is encrypted by default, whether stored, transmitted or processed. This ensures protection even if someone gains access to the underlying infrastructure. TOPdesk relies on this platform-level encryption to mitigate the risk of unauthorized access or data theft.
The following steps have been implemented, alongside other safeguards we maintain to ensure data security:
- All customer data is hosted on Microsoft Azure and data is encrypted data at rest, in transit and in use;
- TOPdesk uses well-protected data centers to host your TOPdesk environment(s). There's a layered approach to physical security to reduce the risk of unauthorized users gaining physical access to data and the data center resources;
- TOPdesk has Data Processing Agreements (DPA) with our hosting partner. Data center operators are not allowed to handle customer data, and control procedures are in place. The effectiveness of these procedures is regularly audited, and TOPdesk reviews the audit results;
- Additional database encryption is enabled by default on all our hosting locations;
- Key management is managed by Azure Key Vault.

Encrypted connections
A related risk to theft of stored data, is interception of data before it is stored. This risk is covered by only allowing encrypted connections (HTTPS) with TOPdesk SaaS environments. HSTS preloading ensures all connections are automatically started using HTTPS by all common browsers.
Regular checks determine whether there are known errors in used communication protocols, after which unsafe protocols are disabled as soon as possible. These measures resulted in an A+ score for the TOPdesk SaaS SSL certificate on Qualys SSL Labs, an independent party that assesses the strength of secure connections.
Exit strategy
Data saved in your TOPdesk environment remains your property. We offer a default and easy way to retrieve your data from our software, when you terminate your contract with us. You can, at any time, download all your uploaded attachments via your TOPdesk environment.
After terminating your contract, we delete your data. The taken backups are kept for a maximum of 90 days and removed after this period. To ensure that your data is completely deleted, we have an automatic system with built-in control mechanism for the deletion. We also have a monitoring system that actively scans folders, databases and live environments for data that should have been removed.
If you have not already downloaded your data before your contract ended, one of your SaaS Main Contacts can contact TOPdesk Support to request a copy of your data from the backup. Upon this request, we’ll send you the data as soon as possible through a secure connection. All data comes in a regular file format.
Contact us
If you have any questions about our SaaS hosting, don’t hesitate to contact TOPdesk Support for more information.
Responsible disclosure
We appreciate customers and security researchers reporting vulnerabilities in our software and infrastructure to us.
If you plan to execute a test on our product or SaaS infrastructure, please contact our Support department and ask for the collaboration agreement for penetration tests, that we have in place for this purpose. It provides guidelines on how to responsibly test our services and work together with us, which for instance prevents our security team from interfering with your tests when detected by our monitoring.
Read more about how to report findings on our Coordinated Vulnerability Disclosure page.
If you have any questions about our SaaS hosting, don’t hesitate to contact TOPdesk Support for more information.

Response time
All security incidents are treated with high priority. Our Support team is trained in recognizing security incidents and will immediately escalate these requests to a security expert. You can find more information about incident response procedures on our Tech blog.
We aim to provide customers with an indication on the severity and possible mitigating steps within 1 working day. For the fastest response, please call our Support team to report a possible security issue. You can also report a security issue in our customer portal (My TOPdesk) or send an e-mail to security@topdesk.com.
If a modification in the product is necessary to remedy a vulnerability, we start working on that immediately and aim to incorporate it in the next release of our product.